COMPUTER FORENSICS
Computers hold vast amounts of information that can be crucial to just about any case imaginable. Computer forensics can help find that data “gold,” potentially even if deleted.
The term “forensics” is defined as “the application of scientific knowledge to legal problems” (Merriam-Webster’s Dictionary). Digital forensics professionals, by that definition, apply their knowledge of computer science to answer questions in legal cases: Did the person search for “murder” on their computer? Are there any illegal images on a computer, and if so, how did they get there? What are the contents of the incriminating (but deleted) email that person A sent to person B? Was this computer used to steal intellectual property documents from the company? These are just some of the many questions that can be answered through the science of computer forensics.
At digit diver we utilize the latest computer forensics software and hardware to examine digital evidence. Perhaps even more importantly, we have received countless hours of training to ensure that not only do we follow best practices for digital evidence handling, but that we also use the latest innovative methods for acquiring, processing and analyzing that evidence.
Over time we have earned several highly respected certifications within the digital forensics community. Among them is the Certified Forensic Computer Examiner (CFCE) certification from the International Association of Computer Investigative Specialists (IACIS). This program involves rigorous, multi-stage training over a significant period of time (often 5-6 months). While certification is not a guarantee that someone is an expert in this field, it does demonstrate a level of competency you should expect from a digital forensics professional.
Computer forensics has been used to refer to the general process of recovering deleted, corrupted or otherwise inaccessible computer files. And so in the case where a computer is not involved in a legal case, the term “computer forensics” is not technically correct, but the process for recovering these files is very similar. In these cases we call the process Data Recovery. There are a few factors which play into whether files can be recovered or not (such as how long ago the files were deleted, or if a solid state drive was used, etc.), but there is a good chance we may be able to recover the files.
CLOUD FORENSICS
Cloud Forensics is an emerging area of computer forensic services that we provide. The “cloud” is the storage of digital information through online service providers like Apple’s iCloud, Google Chromebooks, Microsoft Teams and others. The basis of cloud computing is that while a person accesses the data seemingly on their computer, the data is actually located on a server hosted by one of the online service providers. Naturally this presents a challenge to digital forensics professionals because we don’t have the physical server in our custody, so we must access it remotely. As a result, we may only get a fraction of the data we need, or maybe no data at all. Cloud computing is continually expanding, and it may one day be the standard for how we use our computers, so it is imperative that we in digital forensics develop methods for obtaining that data.
EMAIL ANALYSIS
Email Analysis is another offshoot of computer forensics the we offer, and it has become vital to many legal cases. We humans may not write physical letters to people anymore, but we sure do use email. It’s quite likely we use email far more than phone calls for communication. Because of this, email has become a rich source of evidence for cases.
SOCIAL MEDIA INVESTIGATIONS
We also offer Social Media Investigations for any type of case. It is often surprising (shocking?) how much information people voluntarily post through their social media accounts. This can be yet another great source of digital evidence, but how does one go about getting it? Social media content shares similar challenges to cloud computing, in that the content is often stored on servers controlled by the social media developers and not on the user’s device. Other challenges involve the use of anonymizing services like the TOR (The Onion Router) network and virtual private network (VPN) software, both of which are used to hide the computer’s originating IP address and further complicate such investigations. In spite of the challenges, we have developed expertise over the years investigating social media cases that often prove successful.
ON-SITE COLLECTION AND ANALYSIS
An often overlooked but no less important step in digital forensics is On-Site Collection and Analysis. For this service, we make a forensic copy of the computer(s)/server(s) at the place where they are used, very often while they are still powered on. This step is critical in cases where the computer network has been breached from an outside intrusion or infected by ransomware. In addition to making a forensic copy of the hard drive(s), we also create a copy of the computer’s RAM (or memory) where important clues about the intrusion, infection or other problem are likely to be. These clues may be passwords, encryption or decryption keys, browsing history, network communications with outside computers and many others. But computer memory is only temporary storage and releases its contents when the computer is powered off. Once the computer/server is turned off, these clues may no longer be available for examination. There are many scenarios where this service may be useful to you, so we encourage you to call us if you have any questions about it.
+ + +
SIDE NOTE: DATA INTEGRITY
One of the most important concepts in digital forensics is data integrity – making sure the data does not change during any part of the investigative process. One way we do this is by using math calculations called hash values to determine the unique value of a file. If a forensic copy of a hard drive was completed correctly, then the hash value of both the original hard drive and the forensic copy should match, meaning that no changes were made. Here’s a visual example of what we mean.
Below is Van Gogh’s Starry Night painting. Image #1 is the original. For Image #2, we erased 1 pixel from the image (seen in the circled close-up). We then used an application to determine the hash value – the unique “fingerprint” – of each file. Below each image is its unique hash value. (“MD5” refers to one type of hash calculation used.)
Image #1

Image #2
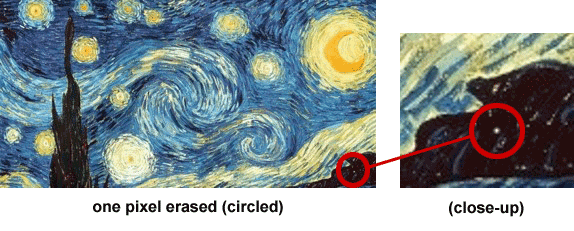
As you might imagine, the hash values are different because of the change we made. What may be surprising, however, is how much the values actually changed. The values are dramatically different.
When we make forensic copies of computer hard drives, it is not uncommon for the hard drive to contain 400,000 files or more. This hash value of the hard drive becomes even more important when we make the forensic copy. Assuming the hash value of the copy matches the original, we are able to prove through hash values that not only were no files altered, but not even a single pixel of one photo was changed.
This is just one of several ways computer forensic practitioners are able to maintain the integrity of the evidence.
+ + +
If you have any questions about Computer Forensics or any of our related services, please contact us to find out how we may be able to help you.
